What are computer security and its types?

There are 5 types of computer security. They are
Information security |
It is the process of securing information from unauthorized access, deletion, and modification. |
Application security |
It is the process of securing an application by formulating security features to prevent Cyber threats likely SQL injection, DoS attacks, data breaches, etc. |
Computer security |
It is the process of securing a standalone machine by keeping it updated and covered. |
Network security |
It is the process of securing both the software and hardware technologies. |
Cyber security |
This process is defined as the process of protecting computer systems that will be communicative over the computer networks. |
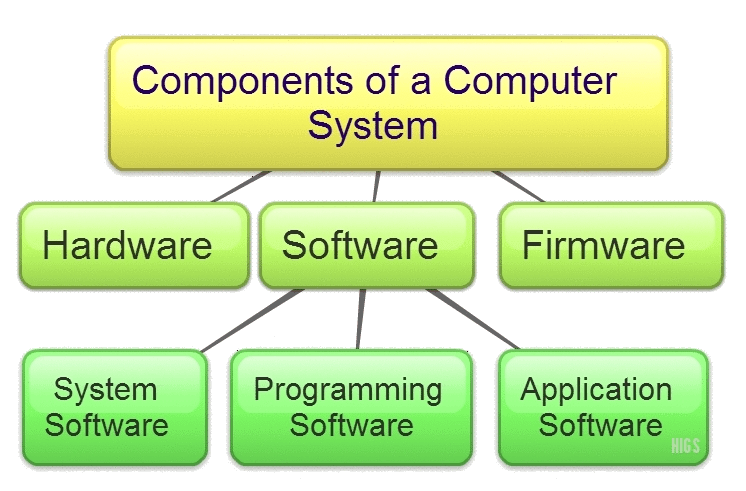
Components of a computer system
The parts of the computer that has to be protected are,
Hardware
The physical part of the computer such as the system memory and disk drive.
Firmware
Permanent software that is fixed into nonvolatile memory of the hardware device and is mostly invisible to the user.
Software
The programming that offers services such as word processors, operating systems, the internet browser to the user.
Confidentiality
It is to make sure that the information is available only to the intended audience.
Integrity
It is to protect information from being modified by unofficial parties.
Availability
It is the method of protecting information from being modified by unauthorized parties.
Computer security threats

Computer security threats are possibly harming the functions of the computer. Presently, cyber threats are continually increasing in the digital world. The most harmful type of computer security is:
Viruses:
A computer virus is a malicious program that is loaded into the user's computer with the knowledge of the user. It replicates on its own and infects the programs on the PC of the user.
Computer worm:
A computer worm is a software program that can copy itself from one computer to another without human interaction.
Phishing:
Unfortunately, Phishing is very easy to perform. You are mistaken into thinking it is the real mail and you may enter your personal information.
Computer security practices
Computer security practices are highly important in today’s life. So, we have given some of the computer security practices to be carried out.
You can secure your computer physically by,
- Installing reputable, reliable security and anti-virus software.
- Firewall activation will act as a security guard among the internet and your local area network.
- Stay up-to-date to know about the latest updates about the software and news surrounding your devices and perform software updates as soon as they become available.
- Always avoid clicking on email attachments unless you know the source.
- You can change your password regularly by using unique names, numbers, and case types.
- Use your internet with much caution and just ignore pop-ups, drive-by downloads while surfing.
- Just carry out regular system scans and periodic system backup.
PhD in Computer security
PhD in computer security is a doctoral research program that is a comprehensive, multidisciplinary research program that prepares graduates for key positions in academia, in federal, state, and local government agencies, and in business and industry.
our team is currently engaged with plenty of research paper projects such as in Big data, Artificial intelligence, Greenhouse, Thermal engineering , Water resource, Telecommunication , Biosensors, Antenna, Wireless Communication, Marketing , Finance, Accounts,
Organizational behavior ,
Structural Engineering ,
NLP ,
IoT ,
Image Processing,
Cloud Computing ,
Signal Processing,
Microwave in Electromagnetic ,
Control System,
Power Systems ,
HRM,
Concrete based,
And more.